© 2019 - estasir
Linksys Hacked Firmware
Posted on by admin
Asus Vulnerability Warning A couple of recent news items involving hackers and a series of popular routers caught our attention, and we’d like to tell you how FlashRouters can keep you safe from these all-too-common attacks and firmware security holes. A Spate of Recent Router Hacks This is not the first time similar firmware issues linked to the have appeared. Including cloud based activities like Asus’ AiCloud with limited security at the base of your network is not recommended as it opens up not just an individual device bu the entire network to major possible security cracks and damage. While not included in this story, and is also not innocent of similar firmware issues.
Your Wi-Fi router, sitting in the corner of your home accumulating dust and unpatched security flaws, provides an attractive target for hackers. Including, according to a new WikiLeaks release, the CIA. On Thursday, WikiLeaks published a detailed a set of descriptions and documentation for the CIA's.
Linksys Wrt54g Firmware Download
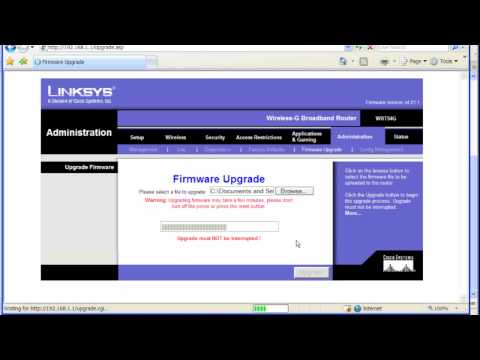
Linksys Firmware Update Wrt54g
They both have had very serious similar issues in the very recent past. To start with, that has affected at least a thousand different home and small office Linksys routers, including the E1000, the E1200, and the E2400.
Linksys Router Hacked Firmware
Johannes Ullrich of the Sans Institute described the depth of the issue in, which detailed the worm’s method of attack, and the ways in which the worm self-replicates by taking advantage of code-execution vulnerability in the device’s original firmware. Then there was an: only a few days after the Linksys exploit revelation, a researcher named Kyle Lovett publicly exposed a major vulnerability in a number of heavy duty Asus routers and their faulty firmwares. In fact, the image above is of an anonymous message that reached at least one Asus user with this very same firmware vulnerability, warning users that the exploit leaves them open to hacking by “anyone in the world with an internet connection.” Lovett was only moved to publish the exploit after he privately contacted Asus with the information. The router company dismissed the problem as “not an issue”, a dismissal with which Lovett evidently disagreed. According to Ars Technica, potentially affected routers include the “RT-AC66R, RT-AC66U, RT-N66R, RT-N66U, RT-AC56U, RT-N56R, RT-N56U, RT-N14U, RT-N16, and RT-N16R.” DD-WRT & Tomato Linksys/Asus Routers Security Fixes. Asus RT-AC66U Upgraded Features These particular stories made us sit up and take notice, because there are a few routers listed as vulnerable that are included in our line, such as the, the and the.
Coments are closed